Check Point Full Disk Encryption For Mac
- Check Point Full Disk Encryption For Mac Mac
- Filevault Disk Encryption Mac
- Disk Encryption Vs File Encryption
Open Start > Programs > Check Point > Full Disk Encryption > Full Disk Encryption Dynamic Mount Utility. The utility shows a list of all connected hard drives. Click the drive to mount. If mounting fails, click Browse and select the correct recovery file. Click the drive to mount. May 28, 2008 - Check Point Technologies on Wednesday unveiled Check Point Full Disk Encryption for Mac OS X, offering users pre-boot authenticated disk.
We use Checkpoint here, and are currently in the process of planning a major from the standalone client to the full console version. They had some issues in the past with the OS X and Windows versions not being in sync, but with the latest release E80 release, the clients are identical. There are still a few gaps, such as not supporting Fusion drives, but overall, things have been great.
Deployment has been simple: We create a composer package that pushes the installer and our installation profile onto the client, and then call a script to run through the pkg installer. It has worked flawlessly for us. As far as management goes, the reason we are moving to the console version is to have better reporting. Currently, the encryption files are written to a File share, and that is all the logging we get. We use the JSS' EA to get a more up to date picture, but with the Console version, it allows for more 'real-time' updates (1-2 minutes). Toshiba satellite c655d s5300 specs.
The stability has been great for us. We have found a few iMacs that shipped to us with bad blocks/sectors that were not picked up by any of our HD diagnostics.
Check Point Full Disk Encryption For Mac Mac
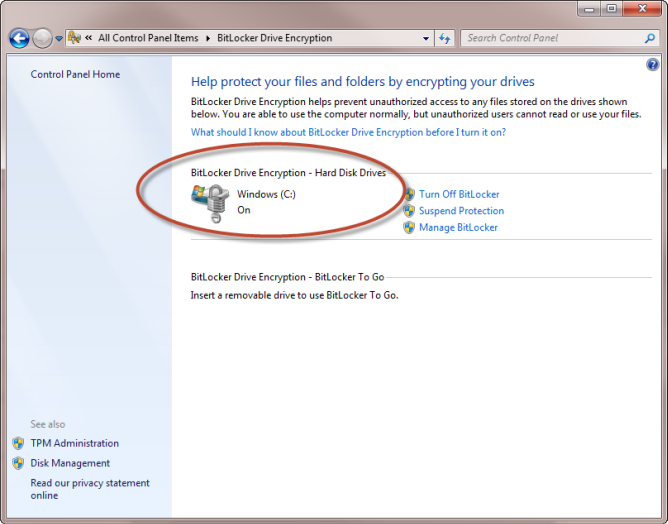
When we have reached out to support, they have been quick to respond. Like I said above, I definitely suggest the web chat as the best option. Reliability has been pretty good. We saw an uptick in 'black screens' that leave the machines in an un-bootable state, but that is more due to the fact that these drives have been encrypted for 4-5 years, and are used 24/7. As far as performance goes, we have noticed that with Checkpoint we are getting about a 1-2% performance hit over FileVault, but nothing that has cause major issues. We are just wrapping up a proof of concept with Checkpoint for Mac and of the options out there I'd say it is by far the best.
Especially if you integrate with AD. The encryption is pretty quick with low overhead after the fact. Deployment is really easy and its in their roadmap to be able to build Mac packages from the console.
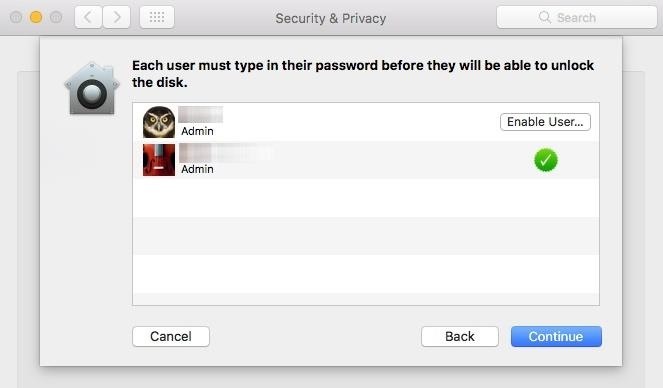
The two biggest sells for me on the product are the preboot single sign on THAT WORKS and the ability of our techs to mount the filesystem while booted from one of our emergency drives. This gives it parity with FileVault, which we can not deploy in our environment. I've been testing it for about a month if you have any specific questions. @iJake That is 100% true. There are some things you can do to mitigate this, using profiles to lock down the 'Security & Privacy' preference pane comes to mind. But, in the end, you are correct. If someone has an administrative account, that is also authorized to unlock the drive, and wants to decrypt the drive, they can.
That said, any of the other solutions allow an administrative account that is authorized to unlock the drive to access, and copy data off of, the encrypted drive - which is the root of what you're trying to prevent. There is a lot of trust/responsibility given to people that have administrative rights to a machine, this is no different. I treat this as an issue with breaking corporate policy. Set up a smart group for machines that are not encrypted and have it mail you on group change. If someone decrypts their machine, give them a very firm warning and re-encrypt the drive. If it happens again, forward the email to your security team or HR and let them discuss the employee's continued future at the company. We didn't Symantec because If I'm remember correctly it has the serious design flaw of not being able to have the machine shut down during initial encryption.
It would break the encryption. Symantec bought PGP, so if you're familiar with that then its what it is. Aside from CheckPoint and FileVault we tested Credant and McAfee.

Filevault Disk Encryption Mac
The Credant had some issues when I first tested it but after those were cleared up it worked pretty well. It just doesn't offer pre boot and that was a no go for me. We use Credant file encryption on our PCs and are quite experienced with it. Its definitely the best option if you want the absolute least change for your customers. McAfee is just not ready on the Mac.
It can't work with local users for pre boot but rather they HAVE to be AD. That eliminates any local admin account you might use. As well, there is no way to mount the filesystem from another drive. I wasn't really a fan of the ePO console as its quite confusing and overcomplicated. I use Symantec Encryption Desktop or PGP. I can provide a list of reasons that you might not want to use it. It takes over the Apple recovery partition and makes it very difficult to boot to another partition although bootcamp supposedly works.
Having User Data on a separate partition is possible but like i said you cannot boot to another OS partition or restore only the OS partition in my few attempts anyway so there is no point in separating user data from the OS. Filevault is not much better for multi-partition stuff either, I found some tool some really smart guy wrote to mount the user data partition, which has to be encrypted separately and mounted separately and it works most of the time, but every now and then i login and the user data partition did not mount, its an easy fix to reboot but kind of clunky. It is very good at finding bad sectors on the disk, the bad news is it usually does not boot when it finds them. It can be very susceptible to OS X updates, read this as might not boot after an update. It only supports 8 keyboard layouts fully, others mostly work but the UK is not one of the supported layouts and if you use the pound symbol in your passphrase you are going to have a bad day. It encrypts a SSD really fast, and the later version encrypts a bit faster on the spinning disks, but 320GB in about 12 hours is what I see and you cannot use the machine during this time on spinning disks because it is so slow. Some firmware updates seem impossible to install because I think the recovery partition and firmware stuff is taken over by boot guard.
Disk Encryption Vs File Encryption
The boot guard password has to be managed separately from the user password. Good or bad you choose, it does not autologin after you type your boot guard password. Good things a user cannot decrypt their drive without herculean efforts. Once its there it does not seem to affect the systems performance, we leave that to SEP.
Having PGP installed on a users computer does get them all to be pretty diligent about connecting their time machine backup disks regularly. In all seriousness though, i have near 1000 users on PGP, we have had a couple dozen or so over the last year that have gotten the no boot symbol, and can that all be blamed on PGP? The disks were replaced and the systems ran fine afterward. From my experience at other accounts that might be a bit high for disk failure although every laptop with a 7200 rpm drive i have ever had has been replaced. I will be starting a couple of projects for a couple of new customers with Checkpoint shortly so I am glad to see the good reviews on it.